Conference Program
Best Paper Award:
Lessons Learned Building a Secure, Network Measurement Framework using Basic NDN
Kathleen Nichols (Pollere, Inc.)
Best Student Paper Award:
Name Space Analysis: Verification of Named Data Network Data Planes
Mohammad Jahanian and K. K. Ramakrishnan (University of California, Riverside)
Overview
Free access to the conference papers maintained in the ACM DL is available now.
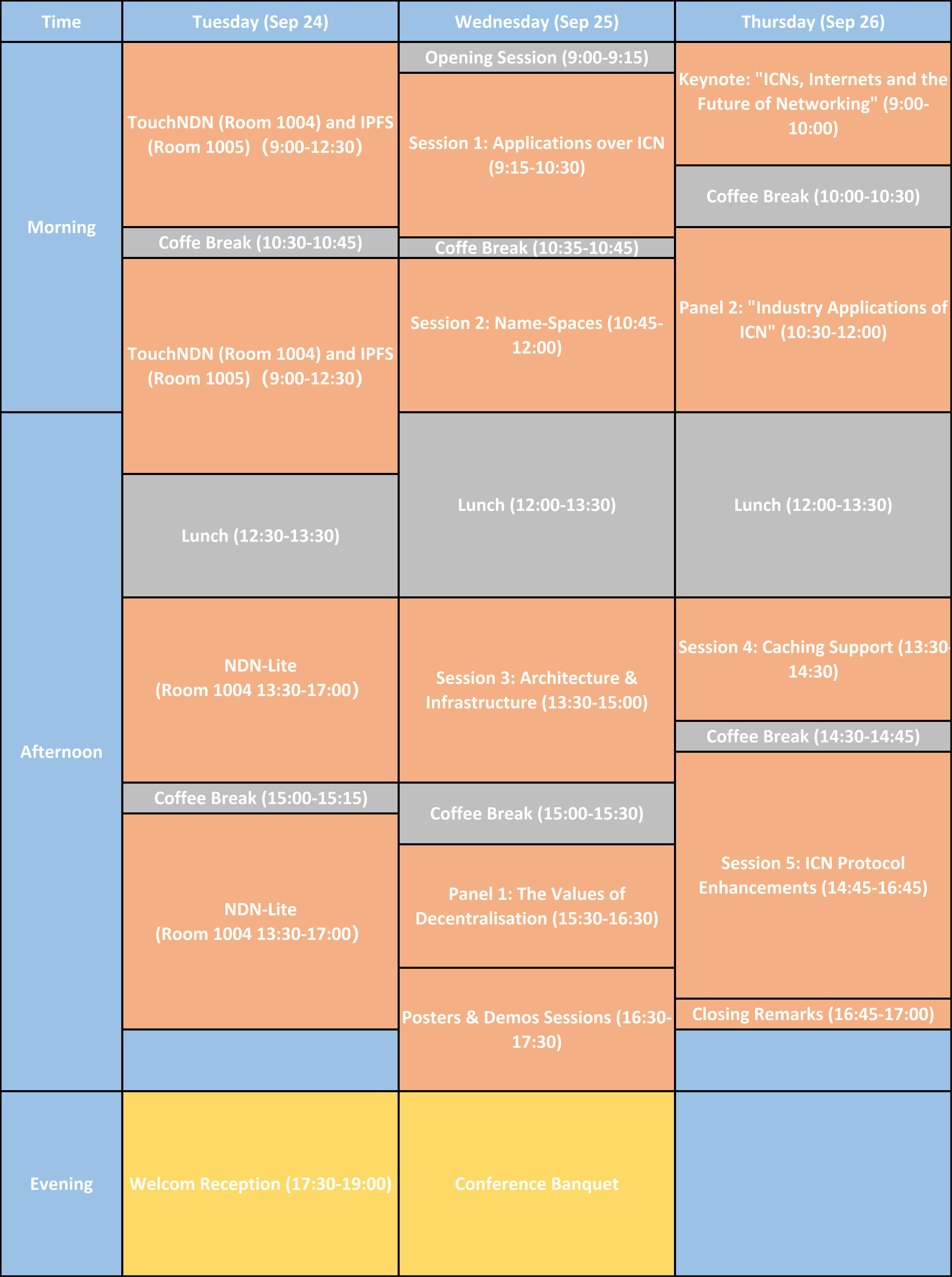
Schedule
-
9:00am - 12:30pm Tutorials: TouchNDN
Room: 1004
- Tutorials: TouchNDN
-
9:00am - 12:30pm Tutorials: IPFS
Room: 1005
- Tutorials: IPFS
-
10:30am - 10:45am Coffee Break
- Coffee Break
-
9:00am - 12:30pm Tutorials: TouchNDN
Room: 1004
- Tutorials: TouchNDN
-
9:00am - 12:30pm Tutorials: IPFS
Room: 1005
- Tutorials: IPFS
-
12:30pm - 13:30pm Lunch
- Lunch
-
13:30pm - 17:00pm Tutorials: NDN-Lite
Room: 1004
- Tutorials: NDN-Lite
-
15:00pm - 15:15pm Coffee Break
- Coffee Break
-
13:30pm - 17:00pm Tutorials: NDN-Lite
Room: 1004
- Tutorials: NDN-Lite
-
17:30pm - 19:00pm Welcome Reception
-
-
9:00am - 9:15am Opening Session
- Opening Session
-
-
-
-
9:15am - 10:30am Session 1: Applications over ICN
Session Chair: Jay Misra
- Session 1: Applications over ICN
-
Dominic Tarr, Erick Lavoie (McGill University), Aljoscha Meyer (TU Berlin), Christian Tschudin (University of Basel)
Abstract: Secure Scuttlebutt (SSB) is a novel peer-to-peer event-sharing protocol and architecture for social apps. In this paper we describe SSB’s features, its operations as well as the rationale behind the design.We also provide a comparison with Named Data Networking (NDN),an existing information-centric networking architecture, to motivate a larger exploration of the design space for information-centric networking primitives by formulating an identity-centric approach.We finally discuss SSB’s limitations and evolution opportunities.
-
Philipp Moll (Alpen-Adria-Universität Klagenfurt), Sebastian Theuermann (Alpen-Adria-Universität Klagenfurt), Natascha Rauscher (NAlpen-Adria-Universität Klagenfurt), Hermann Hellwagner (Alpen-Adria-Universität Klagenfurt), Jeff Burke (UCLA)
Abstract: In this paper, we develop a system for inter-server game state synchronization using the NDN architecture. We use Minecraft as a real-world example of online games and extend Minecraft’s single-server architecture to work as multi-server game. In our prototype,we use two different NDN-based approaches for the dissemination of game state updates in server clusters. In a naive approach, servers request game state updates for small segments of the game worldfrom other servers of the cluster. In an improved approach – the region manifest approach– servers identify changed parts of the world by subscribing to manifest files containing information about world regions managed by the other servers of the cluster. An apparent downside of the NDN approaches is the high overhead when handling small-sized game state updates, but our evaluation shows that NDN already improves on IP-based implementations regarding the resulting traffic volume when three or more servers are involved. Furthermore, caused by NDN’s inherent multicast functionality, the advantage over IP increases with the size of theserver cluster. Moreover, the use of NDN-based approaches leads to benefits beyond traffic reduction only. The name-based host-independent access to world regions allows to scale server clusters easier.
-
Ashlesh Gawande (University of Memphis), Jeremy Clark (University of Memphis), Damian Coomes (University of Memphis), Lan Wang (University of Memphis)
Abstract: Named Data Networking (NDN) thrives in peer-to-peer data sharing
scenarios, through naming data and decoupling data from its
containers. Meanwhile, social media applications have come under
increased criticism for excessive centralization and opacity.
We present npChat, an Android application that allows users to
capture and share multimedia with friends in a secure and fully
decentralized way, while still giving users complete control over
their data.We propose using namespaces owned by users instead of
a shared application namespace and establish trust using multiple
trust models. We use an application-level pub-sub model to share
friend information and publish data, as well as a per-object access
control scheme to share content with selected friends. Our evaluation
demonstrates the application’s data sharing performance and
low overhead in various scenarios.
-
10:35am - 10:45am Coffee Break
- Coffee Break
-
10:45am - 12:00pm Session 2: Name-Spaces
Session Chair: Yuki Koizumi
- Session 2: Name-Spaces
-
Jeff Thompson (UCLA REMAP), Peter Gusev (UCLA REMAP), Jeff Burke (UCLA REMAP)
Abstract: The Named Data Networking Common Name Library (NDN-CNL)
is a high-level library that enables applications to work with hierarchical,
named data collections as an abstract interface to NDN’s
request-response protocol. This approach foregrounds the importance
of application-named data in NDN applications and is intended
as an alternative to socket APIs. It aims to simplify programming
of asynchronous applications that use a variety of data-centric
approaches at the same time, including naming conventions for
versioning, segmenting, synchronization, name-based access control,
name confidentiality, schematized trust, as well as standard
features needed in many applications such as interest pipelining
and latest data retrieval. This paper introduces the rationale and
design of the library, shows its use through a series of examples,
and concludes with a brief discussion of future work. Our emphasis
is on introducing the new abstraction, so the library’s internal
implementation is not discussed in detail; source code is available
on Github.1
-
Pouyan Fotouhi Tehrani (Fraunhofer FOKUS), Eric Osterweil (GMU), Jochen Schiller (Freie Universität Berlin), Thomas C. Schmidt (HAW Hamburg), Matthias Waehlisch (Freie Universität Berlin)
Abstract: Names are the cornerstone of every Information-Centric Network
(ICN), nonetheless, namespace management has been by far neglected
in ICN. A global and scalable namespace management approach
is a challenge which not only concerns technical, but also
requires attention to non-technical, e.g., organizational issues. In
this paper, we present both a clear position on namespace management
in ICN and preliminary work on a potential solution. We
conceptualize a namespace management system for hierarchical
names and introduce a prototype for NDN, which leverages existing
DNSSEC equipped DNS infrastructure. Based on this, we
are able to implement both technical and non-technical aspects of
namespace management. We consider lessons learned and pitfalls
from decades of the ever-evolving development of domain name
system. As the de facto standard namespace management for the
Internet, it is an integral orientation factor for both our concept
and its implementation.
-
Mohammad Jahanian (University of California, Riverside), K. K. Ramakrishnan (University of California, Riverside)
Abstract: Named Data Networking (NDN) has a number of forwarding behaviors,
strategies, and protocols proposed by researchers and incorporated
into the codebase, to enable exploiting the full flexibility
and functionality that NDN offers. This additional functionality
introduces complexity, motivating the need for a tool to help reason
about and verify that basic properties of an NDN data plane are
guaranteed. This paper proposes Name Space Analysis (NSA), a
network verification framework to model and analyze NDN data
planes. NSA can take as input one or more snapshots, each representing
a particular state of the data plane. It then provides the
verification result against specified properties. NSA builds on the
theory of Header Space Analysis, and extends it in a number of
ways, e.g., supporting variable-sized headers with flexible formats,
introduction of name space functions, and allowing for name-based
properties such as content reachability and name leakage-freedom.
These important additions reflect the behavior and requirements of
NDN, requiring modeling and verification foundations fundamentally
different from those of traditional host-centric networks. For
example, in name-based networks (NDN), host-to-content reachability
is required, whereas the focus in host-centric networks (IP) is
limited to host-to-host reachability.We have implemented NSA and
identified a number of optimizations to enhance the efficiency of
verification. Results from our evaluations, using snapshots from various
synthetic test cases and the real-world NDN testbed, show how
NSA is effective, in finding errors pertaining to content reachability,
loops, and name leakage, has good performance, and is scalable.
-
12:00pm - 13:30pm Lunch
- Lunch
-
13:30pm - 15:00pm Session 3: Architectures & Infrastructure
Session Chair: Jussi Kangasharju
- Session 3: Architectures & Infrastructure
-
Giovanna Carofiglio (Cisco Systems), Luca Muscariello (Cisco Systems), Jordan Augé (Cisco Systems), Michele Papalini (Cisco Systems), Mauro Sardara (Cisco Systems), Alberto Compagno (Cisco Systems)
Abstract: Information-Centric Networking (ICN) embraces a family of network
architectures rethinking Internet communication principles
around named-data. After several years of research and the emergence
of a few popular proposals, the idea to replace the Internet
protocol with data-centric networking remains a subject of debate.
ICN advantages have been advocated in the context of 5G networks
for the support of highly mobile, multi-access/source and latencyminimal
patterns of communications. However, large scale testing
and insertion in operational networks are yet to happen, likely due
to the lack of a clear incremental deployment strategy. In this paper,
we analyze a recent proposal Hybrid-ICN (hICN), an ICN integration
inside IP (rather that over/ under/ in place of) that has the
ambition to trade-off no ICN architectural principles. By reusing
existing packet formats, hICN brings innovation inside the IP stack,
requiring minimal software upgrades and guaranteeing transparent
interconnection with existing IP networks.
We describe the architecture and use the open source implementation
to test hICN in the open Internet to validate its short-term
deployability. Further, we consider linear video streaming over mobile
wireless heterogeneous networks as use case to highlight hICN
advantages compared to TCP/IP counterpart.
-
Michał Król (University College London), Spyridon Mastorakis (UCLA), Dave Oran (Network Systems Research & Design), Dirk Kutscher (University of Applied Sciences Emden/Leer)
Abstract: Modern distributed computing frameworks and domain-specific
languages provide a convenient and robust way to structure large
distributed applications and deploy them on either data center or
edge computing environments. The current systems suffer however
from the need for a complex underlay of services to allow
them to run effectively on existing Internet protocols. These services
include centralized schedulers, DNS-based name translation,
stateful load balancers, and heavy-weight transport protocols. In
contrast, ICN-oriented remote invocation methodologies provide
an attractive match for current distributed programming languages
by supporting both functional programming and stateful objects
such as Actors. In this paper we design a computation graph representation
for distributed programs, realize it using Conflict-free
Replicated Data Types (CRDTs) as the underlying data structures,
and employ RICE (Remote Method Invocation for ICN) as the execution
environment. We show using NDNSim simulations that it
provides attractive benefits in simplicity, performance, and failure
resilience.
-
Onur Ascigil (University College London), Sergi Rene (University College London), Michał Król (University College London), George Pavlou (University College London), Lixia Zhang (UCLA), Toru Hasegawa (Osaka University), Yuki Koizumi (Osaka University), Kentaro Kita (Osaka University)
Abstract: In the current Internet, content delivery, e.g., video-on-demand
(VoD), at scale is associated with a large distributed infrastructure
which requires considerable investment. Content Providers
(CPs) typically resort to third-party Content Distribution Networks
(CDNs) or build their own expensive content delivery infrastructure
in order to cope with the peak demand and maintain sucient
quality-of-service (QoS), while Internet Service Providers (ISPs)
need to overprovision their networks. In this paper we take a rst
step towards designing a system that uses storage space of users
as CDN caches and deliver content with sucient (i.e., CDN-like)
quality while rewarding users for their resource usage as in a content
retrieval marketplace. As a possible candidate for such a system,
we consider recent P2P storage and delivery systems that have
adopted new mechanisms such as rewarding of useful work (e.g.,
storage) while ensuring fairness and accountability through cryptographic
proofs. In this paper, we experiment with the popular
Interplanetary File System (IPFS) and investigate its performance in
delivering VoD content locally within an ISP. Our ndings suggest
that operating IPFS (operating on top of IP) has its performance
limitations and complementing it with an ICN network layer can
signicantly improve the delivery quality. We then propose and
compare several forwarding strategies for ICN which can eciently
route requests and balance the load between peers with limited
uplink resources.
-
15:00pm - 15:30pm Coffee Break
- Coffee Break
-
15:30pm - 16:30pm Panel 1: The Values of Decentralisation
Panel Moderator : Christian Tschudin
- Panel 1: The Values of Decentralisation
-
16:15pm - 17:30pm Posters & Demo Sessions
- Posters & Demo Sessions
-
Conference Banquet
-
-
-
9:00am - 10:00am Keynote: "ICNs, Internets and the Future of Networking"
Speaker : David Clark, MIT
- Keynote: "ICNs, Internets and the Future of Networking"
-
10:00am - 10:30am Coffee Break
- Coffee Break
-
10:30am - 12:00pm Panel 2: "Industry Applications of ICN"
Panel Moderator: Dirk Kutscher, University of Applied Sciences Emden/Leer
- Panel 2: "Industry Applications of ICN"
-
Recent ICN research has produced various platforms for experimentation and application development. One welcome development consists of initial ICN deployment mechanisms that do not require a forklift replacement of large parts of the Internet. At the same time, new technologies and use cases, such as edge computing, massively scalable multiparty communication, and linear video distribution, impose challenges on the existing infrastructure. This panel brings together experts from different application domains in order to discuss pain points with current systems, opportunities and promising results for building specific applications with ICN, and challenges, shortcomings, and ideas for future evolution of ICN.
Panelist : Richard Chow(University Research Manager and Scientist, Intel Labs), David Wei Liang (Vice-Director of China Telecom Research Institute), Kathie Nichols (CTO at Pollere Inc.), Kent Wu (Director Cloud Computing at Hong Kong Applied Science and Technology Research Institute)
-
12:00pm - 13:30pm Lunch
- Lunch
-
13:30pm - 14:30pm Session 4: Caching Support
Session Chair: Onur Ascigil
- Session 4: Caching Support
-
Eric Newberry (The University of Arizona), Beichuan Zhang (The University of Arizona)
Abstract: The Hadoop Distributed File System (HDFS) is a network file system used to support multiple widely-used big data frameworks that
can scale to run on large clusters. In this paper, we evaluate the
effectiveness of using in-network caching on switches in HDFSsupported
clusters in order to reduce per-link bandwidth usage in
the network. We discovered that some applications featured large
amounts of data requested by multiple clients and that, by caching
read data in the network, the average per-link bandwidth usage
of read operations in these applications could be reduced by more
than half. We also found that the choice of cache replacement policy
could have a significant impact on caching effectiveness in this
environment, with LIRS and ARC generally performing the best
for larger and smaller cache sizes, respectively. Moreover, given
the structure of HDFS write operations, we developed a mechanism
to reduce the total per-link bandwidth usage of HDFS write
operations by replacing write pipelining with multicast. In order
to evaluate in-network caching potential, we developed a simulator
to replay real traces through a fat tree network simulating the
caching architecture used in the Named Data Networking (NDN)
information-centric networking (ICN) architecture. Our results
suggest that ICN-style in-network caching can provide significant
benefits to HDFS-supported big data clusters, justifying future work
to apply ICN architectures to cluster environments.
-
Jakob Pfender (Victoria University of Wellington), Alvin Valera (Victoria University of Wellington), Winston K. G. Seah (Victoria University of Wellington)
Abstract: In Information-Centric Networking (ICN), the ability to cache content
at multiple points in the network is one of the most important
factors in the speed and reliability of content delivery. However, in
the constrained environment of the Internet of Things (IoT), memory
is often a scarce resource, which means that particular focus
needs to be placed on how to use the available memory for caching.
Previous research has shown that caching heuristics that take network
topology into account have great promise, but are often not
feasible for use in the IoT as they typically incur high overheads
or require extensive knowledge of the topology. We introduce a
simple content caching strategy called Approximate Betweenness
Centrality (ABC), which makes use of the topology-based heuristics
of existing strategies, but requires no knowledge of the network
and incurs no communications overhead. We compare this new
strategy to several existing ICN caching strategies and evaluate
its effectiveness using real IoT devices in a large physical testbed.
We show that our lightweight approach can deliver results that are
comparable to those of more expensive strategies while incurring
almost no additional costs.
-
14:30pm - 14:45pm Coffee Break
- Coffee Break
-
14:45pm - 16:45pm Session 5: ICN Protocol Enhancements
Session Chair: Alex Afanasyev
- Session 5: ICN Protocol Enhancements
-
Kathleen Nichols (Pollere, Inc.)
Abstract: The Named-Data Networking Project has moved from a multiuniversity
NSF-funded Future Internet Architecture project to an
open source codebase with world wide contributors and a growing
body of applications. Researchers have applied NDN to applications
like lighting control, vehicular communications, and augmented reality
but more work is needed to make the data-centric and security
features of NDN accessible. Users are currently required to become
experts on the internals of the codebase, a difficult task further complicated
by the lack of well-documented examples and the project
adding new features. While implementing a secure, distributed
network measurement framework for NDN, we encountered two
major difficulties: the lack of a library of application-usable communications
models (built on top of the NDN layer) and the difficulty
of integrating trust rules with the NDN codebase.
This paper describes our NDN network measurement framework
and the co-developed tools that implement its secure, publish/subscribe
communications model. Our goals are both to present the
network measurement framework and to motivate developers to
evolve NDN by creating frameworks, libraries, and includible headers
rather than bloating NDN’s waist.
-
Sanjeev Kaushik Ramani (Florida International University), Reza Tourani (Saint Louis University), George Torres (New Mexico State University), Satyajayant Misra (New Mexico State University), Alexander Afanasyev (Florida International University)
Abstract: The Named Data Networking architecture mandates cryptographic
signatures of packets at the network layer. Traditional RSA and
ECDSA public key signatures require obtaining signer’s NDN certificate
(and, if needed, the next-level certificates of the trust chain)
to validate the signatures. This potentially creates two problems.
First, the communication channels must be active in order to retrieve
the certificates, which is not always the case in disruptive and
ad hoc environments. Second, the certificate identifies the individual
producer and thus producer anonymity cannot be guaranteed
if necessary.
In this paper, we present NDN-ABS, an alternative NDN signatures
design based on the attribute-based signatures, to addresses
both these problems. With NDN-ABS, data packets can be verified
without the need for any network retrieval (provided the trust
anchor is pre-configured) and attributes can be designed to only
identify application-defined high-level producer anonymity sets,
thus ensuring individual producer’s anonymity. The paper uses an
illustrative smart-campus environment to define and evaluate the
design and highlight how the NDN trust schema can manage the
validity of NDN-ABS signatures. The paper also discusses performance
limitations of ABS and potential ways they can be overcome
in a production environment.
-
Hauke Petersen (Freie Universität Berlin), Peter Kietzmann (HAW Hamburg), Cenk Gündogan (HAW Hamburg), Thomas C. Schmidt (HAW Hamburg), Matthias Wählisch (Freie Universität Berlin)
Abstract: Bluetooth (BT) mesh is a new mode of BT operation for low-energy
devices that offers group-based publish-subscribe as a network
service with additional caching capabilities. These features resemble
concepts of information-centric networking (ICN), and the analogy
to ICN has been repeatedly drawn in the BT community. In this
paper, we compare BT mesh with ICN both conceptually and in
real-world experiments. We contrast both architectures and their
design decisions in detail. Experiments are performed on an IoT
testbed using NDN/CCNx and BT mesh on constrained RIOT nodes.
Our findings indicate significant differences both in concepts and
in real-world performance. Supported by new insights, we identify
synergies and sketch a design of a BT-ICN that benefits from both
worlds.
-
Cenk Gündoğan (HAW Hamburg), Jakob Pfender (Victoria University of Wellington), Michael Frey (Safety IO), Thomas C. Schmidt (HAW Hamburg), Felix Shzu-Juraschek (Safety IO), Matthias Wählisch (Freie Universität Berlin)
Abstract: Quality of Service (QoS) in the IP world mainly manages forwarding
resources, i.e., link capacities and buffer spaces. In addition,
Information Centric Networking (ICN) offers resource dimensions
such as in-network caches and forwarding state. In constrained
wireless networks, these resources are scarce with a potentially
high impact due to lossy radio transmission. In this paper, we explore
the two basic service qualities (i) prompt and (ii) reliable traffic
forwarding for the case of NDN. The resources we take into account
are forwarding and queuing priorities, as well as the utilization
of caches and of forwarding state space. We treat QoS resources
not only in isolation, but correlate their use on local nodes and
between network members. Network-wide coordination is based
on simple, predefined QoS code points. Our findings indicate that
coordinated QoS management in ICN is more than the sum of its
parts and exceeds the impact QoS can have in the IP world.
-
16:45pm - 17:00pm Closing Remarks
- Closing Remarks
List of Accepted Posters
-
Muktadir Chowdhury (University Of Memphis), Junaid Ahmed Khan (University of Memphis), Lan Wang (University Of Memphis)
Abstract: Routing solutions for NDN VANET that use location information
can be inadequate when such information is unavailable
or when the vehicles’ locations change very fast. In this paper,
we propose CCLF, a novel forwarding strategy to address this
challenge. In addition to leveraging vehicle location information,
CCLF takes into account content-based connectivity
information, i.e., Interest satisfaction ratio for each name
prefix, in its forwarding decisions. By keeping track of content
connectivity and giving higher priority to vehicles with
better content connectivity to forward Interests, CCLF not
only reduces Interest flooding when location information is
unknown or inaccurate, but also increases data fetching rate.
-
Shanshan Shi (Computer Network Information Center, Chinese Academy of Sciences, University of Chinese Academy of Sciences), Jun Li (Computer Network Information Center, Chinese Academy of Sciences), Haibo Wu (Computer Network Information Center, Chinese Academy of Sciences)
Abstract: The transmission performance of flows in NDN is greatly
dependent on congestion control algorithms. However, current
congestion control schemes for NDN are not designed
to distinguish flows of different type, and they are relatively
conservative for mice flows. This poster proposes a Packet-
Pair based startup for NDN congestion control schemes, by
exploiting the available bandwidth estimation during the
flow startup, to approach the maximum throughput faster.
Thus, this technique can improve the transmission efficiency
of mice flows without harming elephant flows. We evaluate
our proposal on ndnSIM and prove its effectiveness.
-
Yating Yang (Beijing Institute of Technology), Tian Song (Beijing Institute of Technology)
Abstract: In-network caching significantly improves the efficiency of data
transmission in ICN by replicating requested data for future reaccess.
In this work, we shift our focus on once-request data, which
cannot be re-used and would lead to under-utilization of in-network
caching.We present a name feature-based online learning approach
to recognizing and filtering once-request data when making caching
decision. It can dynamically update its parameters through online
observation on previous recognition. Evaluation results show that
our learning approach can recognize once-request data with more
than 80% accuracy. By filtering those data, 76% cache replacement
operations are saved and cache hit ratio is increased by 151%.
-
Min Wook Kang (Soongsil University), Dong Yeong Seo (Soongsil University), Yun Won Chung (Soongsil University)
Abstract: Opportunistic routing protocols, such as delay tolerant networks (DTN), can be used to enable information centric networking (ICN) in disaster environments. Existing approaches using DTN for ICN suffers from message overhead due to the mobility of sparsely populated mobile nodes and overall performance degradation. We therefore propose an efficient opportunistic routing protocol for ICN to reduce message overhead and improve delivery probability, too. Performance evaluation results thorough simulation show that the proposed protocol has better delivery probability and overhead ratio than conventional protocol.
-
Ngoc-Thanh Dinh (Soongsil University, Seoul, Korea), Nhu-Ngoc Dao (Chung-Ang University, Seoul, Korea), Younghan Kim (Soongsil University, Seoul, Korea)
Abstract: The per-packet signature mechanism in NDN is a basic mechanism
to provide in-network security. Consumers can validate provenance
and integrity with the public key-based signature attached with
each Data packet. However, the creation and validation processes
of signature cause significant performance bottlenecks in both of
consumers and producers. The embedded manifest mechanism was
proposed to ease the signing overhead for streaming data producers;
a signed manifest packet being composed of digests of subsequent
Data packets is inserted per bundle of Data packet while each
Data packet has only its digest as SignatureInfo. For a large file,
the embedded manifest mechanism still needs producers to sign
multiple manifest packets. The basic idea of proposed mechanism,
Canary, is to enable per-segment provenance and data integrity
validation with only one signing operation of producers even for a
large file by exploiting the properties of Merkle tree.
-
Muhammad Atif Ur Rehman (Hongik University Sejong Campus, South Kore), Rehmat Ullah (Hongik University Sejong Campus, South Kore), Byung-Seo Kim (Hongik University Sejong Campus, South Kore)
Abstract: This poster proposes a lite variant of Named Data Networking
(NDN) architecture specially designed for single-channel
cluster-based information-centric wireless sensor networks.
The proposed framework incorporates the fundamental requirement
of short but human-readable names for clusterbased
wireless sensor networks (WSNs) that can fit into
127 bytes Maximum Transmission Unit (MTU) size. As the
nodes in WSN can be heterogeneous in terms of data generation,
therefore, the name integrated lite query structure
in our framework can significantly improve the process of
data collection. Moreover, the proposed forwarding strategy
for inter-cluster and intra-cluster communication may reduce
the unnecessary packet transmissions in the network, which
improve the network performance.
-
Tieying Zhu (Northeast Normal University, China), Haonan Yan (Northeast Normal University, China), Liu Yang (Ericsson(Xi'an) Information Communication Technology Services Co Ltd, Dalian branch), Riming Zhang (Northeast Normal University, China)
Abstract: NDN proposes a data-centric communication model which makes
it possible to fetch data identified by a name carried in Interest
packets. We developed a file sharing application, called ndnShare,
for mobile devices. It supports the name-based information
retrieval and content acquisition between neighbors over Wi-Fi
Direct. It also supports the fuzzy interest name matching based on
a modified version of NFD-Android. The demo provides the basic
flow of the application, from producing interest query to obtaining
files between Android devices.
-
Yong Yoon Shin (ETRI, Korea), Sae Hyong Park (ETRI, Korea), Quang Tung Thai (ETRI, Korea), Sung Hyuk Byun (ETRI, Korea)
Abstract: The per-packet signature mechanism in NDN is a basic mechanism
to provide in-network security. Consumers can validate provenance
and integrity with the public key-based signature attached with
each Data packet. However, the creation and validation processes
of signature cause significant performance bottlenecks in both of
consumers and producers. The embedded manifest mechanism was
proposed to ease the signing overhead for streaming data producers;
a signed manifest packet being composed of digests of subsequent
Data packets is inserted per bundle of Data packet while each
Data packet has only its digest as SignatureInfo. For a large file,
the embedded manifest mechanism still needs producers to sign
multiple manifest packets. The basic idea of proposed mechanism,
Canary, is to enable per-segment provenance and data integrity
validation with only one signing operation of producers even for a
large file by exploiting the properties of Merkle tree.
List of Accepted Demos
-
Yoji Yamamoto (Osaka University), Yuki Koizumi (Osaka University), Toru Hasegawa (Osaka University), Giulio Rossi (Università degli Studi di Roma - Tor Vergata), Andrea Detti (Università degli Studi di Roma - Tor Vergata), Onur Ascigil (University College London), Ioannis Psaras (University College London)
Abstract: The paper describes the prototype of object search service wherein
multiple IoT devices execute the network function of identifying
the object in the specified area.
-
Pouyan Fotouhi Tehrani (Weizenbaum Institut/Fraunhofer FOKUS), Luca Keidel (Freie Universität Berlin), Eric Osterweil (GMU), Jochen Schiller (Freie Universität Berlin), Thomas Schmidt (HAW Hamburg), Matthias Wählisch (Freie Universität Berlin)
Abstract: In this demo, we showcase NDNSSEC. NDNSSEC provides a namespace
management solution for named-data networking (NDN) based
on the DNS ecosystem and its security extensions. Our prototype allows
content consumers to verify the name ownership in commonly
used NDN software.
-
Cenk Gündoğan (HAW Hamburg), Peter Kietzmann (HAW Hamburg), Thomas C. Schmidt (HAW Hamburg), Matthias Wählisch (Freie Universität Berlin)
Abstract: This demo showcases how ICN resource management can service
the needs of very challenged deployments such as constrained
IoT edge networks in disaster scenarios. Using realistic implementations
on RIOT, we demonstrate how very constrained devices
in harsh environments can reliably communicate, provided QoS
measures are in place. These devices gradually invoke traffic flows
of different priority levels, which are displayed in real-time on a
dashboard. In this setup, we contrast regular bulk traffic with degradation
in flow latency and reliability with QoS-enhanced traffic
differentiation and visualize the improved flow resource consumption
of high priority traffic on all nodes.
-
Hauke Petersen (Freie Universität Berlin), Peter Kielmann (HAW Hamburg), Thomas C. Schmidt (HAW Hamburg), Matthias Wählisch (Freie Universität Berlin)
Abstract: Bluetooth Low Energy (BLE) has seen a remarkable adoption and
it is widely available on a variety of devices, such as modern PCs,
smartphones, and battery driven sensors. A great number of software
tools exist already that implement sensor-generic Bluetooth
profiles. On the lower end, BLE features a robust energy efficient
link layer. The technology, however, lacks multi-hop capabilities.
In this demo we showcase a constrained NDN network that utilizes
BLE L2CAP connections for robust communication.We enable
multi-hop topologies and set up an NDN-to-BLE gateway in order
to reuse existing BLE applications that expect GATT payloads.